Scammers are flooding Fb with teams that purport to supply video streaming of funeral companies for the just lately deceased. Family and friends who observe the hyperlinks for the streaming companies are then requested to cough up their bank card data. Just lately, these scammers have branched out into providing faux streaming companies for almost any type of occasion marketed on Fb. Right here’s a more in-depth take a look at the scale of this scheme, and a few findings about who could also be accountable.
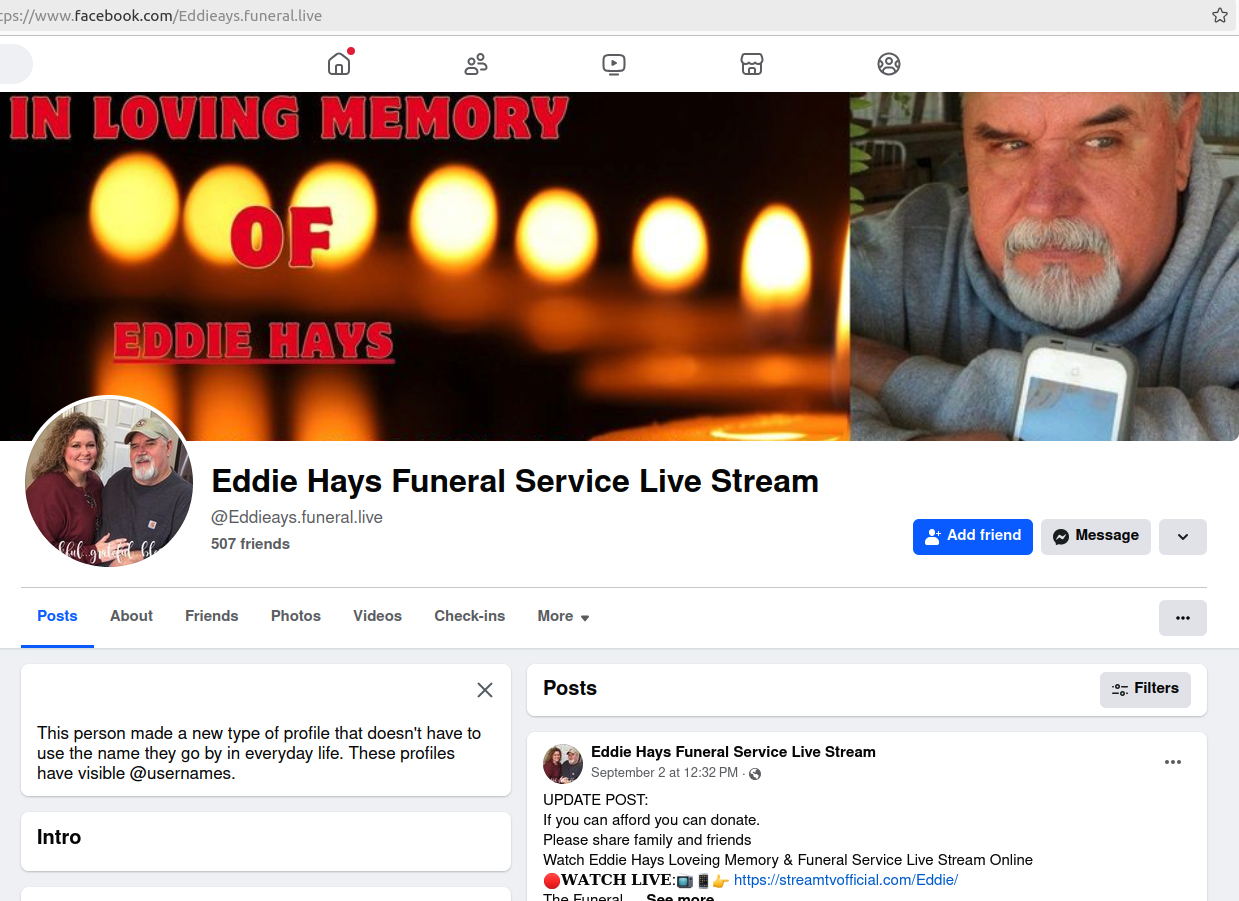
One of many many rip-off funeral group pages on Fb. Clicking to view the “stay stream” of the funeral takes one to a newly registered web site that requests bank card data.
KrebsOnSecurity just lately heard from a reader named George who stated a good friend had simply handed away, and he seen {that a} Fb group had been created in that good friend’s reminiscence. The web page listed the right time and date of the funeral service, which it claimed might be streamed over the Web by following a hyperlink that led to a web page requesting bank card data.
“After I posted in regards to the website, a buddy of mine indicated [the same thing] occurred to her when her good friend handed away two weeks in the past,” George stated.
Looking out Fb/Meta for a number of easy key phrases like “funeral” and “stream” reveals numerous funeral group pages on Fb, a few of them for companies prior to now and others erected for an upcoming funeral.
All of those teams embody pictures of the deceased as their profile picture, and search to funnel customers to a handful of newly-registered video streaming web sites that require a bank card cost earlier than one can proceed. Much more galling, a few of these pages request donations within the identify of the deceased.
It’s not clear what number of Fb customers fall for this rip-off, but it surely’s price noting that many of those faux funeral teams appeal to subscribers from not less than a few of the deceased’s followers, suggesting these customers have subscribed to the teams in anticipation of the service being streamed. It’s additionally unclear how many individuals find yourself lacking a good friend or liked one’s funeral as a result of they mistakenly thought it was being streamed on-line.
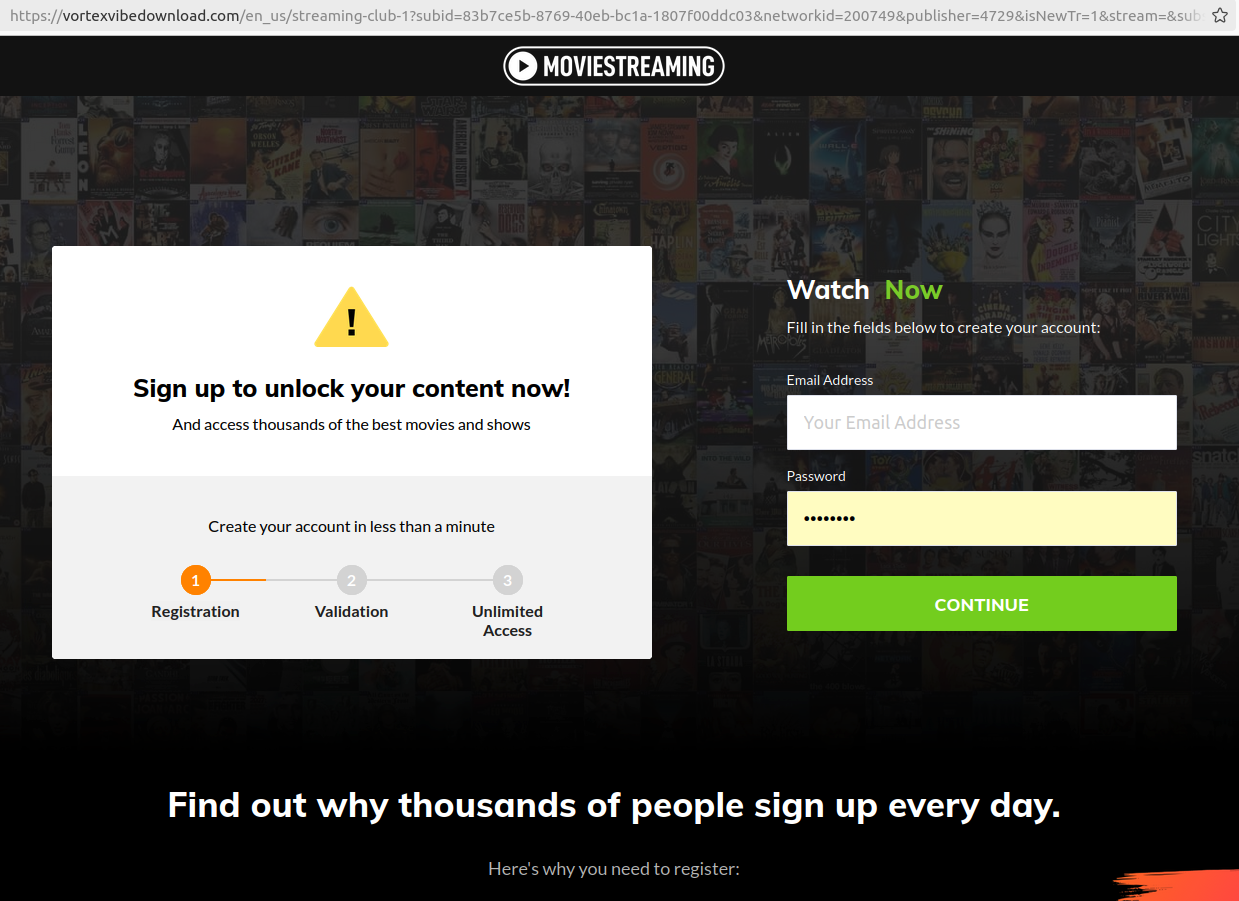
One among many look-alike touchdown pages for video streaming companies linked to rip-off Fb funeral teams.
George stated their good friend’s funeral service web page on Fb included a hyperlink to the supposed live-streamed service at livestreamnow[.]xyz, a site registered in November 2023.
In response to DomainTools.com, the group that registered this area known as “apkdownloadweb,” relies in Rajshahi, Bangladesh, and makes use of the DNS servers of a Internet hosting firm in Bangladesh referred to as webhostbd[.]internet.
A search on “apkdownloadweb” in DomainTools exhibits three domains registered to this entity, together with live24sports[.]xyz and onlinestreaming[.]xyz. Each of these domains additionally used webhostbd[.]internet for DNS. Apkdownloadweb has a Fb web page, which exhibits a lot of “stay video” teasers for sports activities occasions which have already occurred, and says its area is apkdownloadweb[.]com.
Livestreamnow[.]xyz is at present hosted at a Bangladeshi internet hosting supplier named cloudswebserver[.]com, however historic DNS data present this web site additionally used DNS servers from webhostbd[.]internet.
The Web tackle of livestreamnow[.]xyz is 148.251.54.196, on the internet hosting big Hetzner in Germany. DomainTools exhibits this similar Web tackle is dwelling to almost 6,000 different domains (.CSV), together with a whole bunch that reference video streaming phrases, like watchliveon24[.]com and foxsportsplus[.]com.
There are millions of domains at this IP tackle that embody or finish within the letters “bd,” the nation code top-level area for Bangladesh. Though many domains correspond to web sites for electronics shops or blogs about IT subjects, simply as many include a good quantity of placeholder content material (assume “lorem ipsum” textual content on the “contact” web page). In different phrases, the websites seem legit at first look, however upon nearer inspection it’s clear they don’t seem to be at present utilized by lively companies.
The passive DNS data for 148.251.54.196 present a shocking variety of outcomes which might be principally two domains mushed collectively. For instance, there may be watchliveon24[.]com.playehq4ks[.]com, which shows hyperlinks to a number of funeral service streaming teams on Fb.
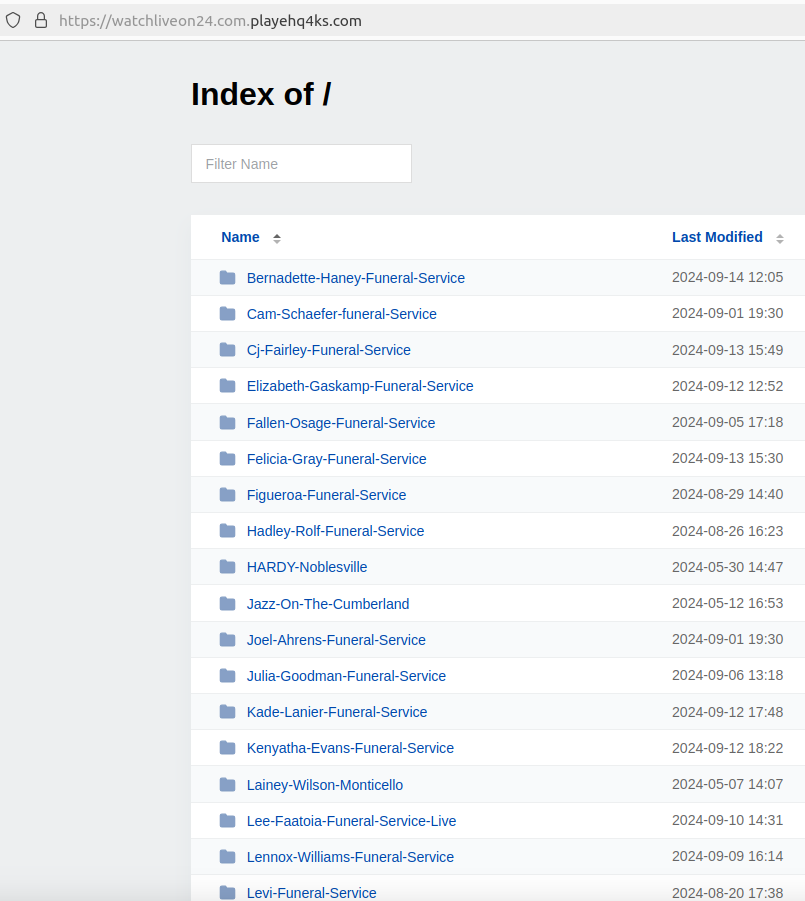
One other mixed area on the identical Web tackle — livestreaming24[.]xyz.allsportslivenow[.]com — lists dozens of hyperlinks to Fb teams for funerals, but in addition for nearly all varieties of occasions which might be introduced or posted about by Fb customers, together with graduations, live shows, award ceremonies, weddings, and rodeos.
Even group occasions promoted by state and native police departments on Fb are truthful recreation for these scammers. A Fb web page maintained by the police drive in Plympton, Mass. for a city social occasion this summer season referred to as Plympton Evening Out was shortly made into two completely different Fb teams that knowledgeable guests they might stream the festivities at both espnstreamlive[.]co or skysports[.]stay.
WHO’S BEHIND THE FAKEBOOK FUNERALS?
Recall that the registrant of livestreamnow[.]xyz — the bogus streaming website linked within the Fb group for George’s late good friend — was a corporation referred to as “Apkdownloadweb.” That entity’s area — apkdownloadweb[.]com — is registered to a Mazidul Islam in Rajshahi, Bangladesh (this area can be utilizing Webhostbd[.]internet DNS servers).
Mazidul Islam’s LinkedIn web page says he’s the organizer of a now defunct IT weblog referred to as gadgetsbiz[.]com, which DomainTools finds was registered to a Mehedi Hasan from Rajshahi, Bangladesh.
To carry this full circle, DomainTools finds the area identify for the DNS supplier on all the above-mentioned websites — webhostbd[.]internet — was initially registered to a Md Mehedi, and to the e-mail tackle webhostbd.internet@gmail.com (“MD” is a standard abbreviation for Muhammad/Mohammod/Muhammed).
A search on that e mail tackle at Constella finds a breached document from the information dealer Apollo.io saying its proprietor’s full identify is Mohammod Mehedi Hasan. Sadly, this isn’t a very distinctive identify in that area of the world.
However as luck would have it, someday final yr the administrator of apkdownloadweb[.]com managed to contaminate their Home windows PC with password-stealing malware. We all know this as a result of the uncooked logs of knowledge stolen from this administrator’s PC had been listed by the breach monitoring service Constella Intelligence [full disclosure: As of this month, Constella is an advertiser on this website].
These so-called “stealer logs” are largely generated by opportunistic infections from information-stealing trojans which might be offered on cybercrime markets. A typical set of logs for a compromised PC will embody any usernames and passwords saved in any browser on the system, in addition to an inventory of current URLs visited and information downloaded.
Malware purveyors will usually deploy infostealer malware by bundling it with “cracked” or pirated software program titles. Certainly, the stealer logs for the administrator of apkdownloadweb[.]com present this person’s PC grew to become contaminated instantly after they downloaded a booby-trapped cell software improvement toolkit.
These stolen credentials point out Apkdownloadweb[.]com is maintained by a 20-something native of Dhaka, Bangladesh named Mohammod Abdullah Khondokar.
The “browser historical past” folder from the admin of Apkdownloadweb exhibits Khondokar just lately left a touch upon the Fb web page of Mohammod Mehedi Hasan, and Khondokar’s Fb profile says the 2 are buddies.
Neither MD Hasan nor MD Abdullah Khondokar responded to requests for remark. KrebsOnSecurity additionally sought remark from Meta.

