ESET researchers uncovered a crimeware marketing campaign that focused purchasers of three Czech banks. The malware used, which we’ve got named NGate, has the distinctive skill to relay information from victims’ fee playing cards, through a malicious app put in on their Android units, to the attacker’s rooted Android telephone.
Key factors of this blogpost:
- Attackers mixed commonplace malicious methods – social engineering, phishing, and Android malware – right into a novel assault state of affairs; we suspect that lure messages have been despatched to random telephone numbers and caught clients of three banks.
- In accordance with ESET Model Intelligence Service information, the group has operated since November 2023 in Czechia, utilizing malicious progressive internet apps (PWAs) and WebAPKs. In March 2024 the group’s method improved by deploying the NGate Android malware.
- Attackers have been capable of clone NFC information from victims’ bodily fee playing cards utilizing NGate and relay this information to an attacker machine that was then capable of emulate the unique card and withdraw cash from an ATM.
- That is the primary time we’ve got seen Android malware with this functionality getting used within the wild.
- Victims didn’t need to root their units.
The first aim of this marketing campaign is to facilitate unauthorized ATM withdrawals from the victims’ financial institution accounts. This was achieved by relaying the close to discipline communication (NFC) information from the victims’ bodily fee playing cards, through their compromised Android smartphones through the use of the NGate Android malware, to the attacker’s machine. The attacker then used this information to carry out ATM transactions. If this technique failed, the attacker had a fallback plan to switch funds from the victims’ accounts to different financial institution accounts.
We haven’t seen this novel NFC relay method in any beforehand found Android malware. The method is predicated on a instrument referred to as NFCGate, designed by college students on the Technical College of Darmstadt, Germany, to seize, analyze, or alter NFC visitors; due to this fact, we named this new malware household NGate.
Overview
Victims downloaded and put in the malware after being deceived into pondering they have been speaking with their financial institution and that their machine was compromised. In actuality, the victims had unknowingly compromised their very own Android units by beforehand downloading and putting in an app from a hyperlink in a misleading SMS message a couple of potential tax return. A brief description of this assault is offered within the video under.
It’s necessary to notice that NGate was by no means obtainable on the official Google Play retailer.
NGate Android malware is expounded to the phishing actions of a risk actor that operated in Czechia since November 2023. Nonetheless, we consider these actions have been placed on maintain following the arrest of a suspect in March 2024.
We first seen the risk actor concentrating on purchasers of outstanding Czech banks beginning on the finish of November 2023. The malware was delivered through short-lived domains impersonating reputable banking web sites or official cell banking apps obtainable on the Google Play retailer, as illustrated in Determine 1. These fraudulent domains have been recognized by way of the ESET Model Intelligence Service, which offers monitoring of threats concentrating on a shopper’s model. Throughout the identical month, we reported our findings to our purchasers.
Victimology
Throughout our investigation, we recognized six completely different NGate apps particularly concentrating on purchasers of three banks in Czechia between November 2023 and March 2024.
In a considerable breakthrough, the Czech police apprehended a 22-year-old, who had been stealing cash from ATMs in Prague. Upon arrest, the suspect had 160,000 Czech korunas in his possession, an quantity equal to over 6,000 euros (roughly US$6,500). The nationality of the arrested particular person has not been disclosed. In accordance with the Czech police, the cash recovered from the suspect was stolen from simply the final three victims, so it’s seemingly that the overall quantity stolen by the risk actor behind this scheme is significantly increased.
Evolution of assault situations
The attackers leveraged the potential of progressive internet apps (PWAs), solely to later refine their methods by using a extra refined model of PWAs referred to as WebAPKs. Finally, the operation culminated within the deployment of NGate malware.
You will need to observe that in the entire assault situations described right here, the sufferer’s machine doesn’t must be rooted, solely the attacker’s machine that emulates the acquired NFC visitors.
Progressive internet apps
Initially, these fraudulent web sites misused PWA know-how. This know-how permits a consumer to put in an app from an internet site through a supported browser; the set up might be triggered both routinely by way of a pop-up notification or manually by choosing the Set up app possibility from the browser’s menu. On Android, supported browsers embrace Chrome, Firefox, Edge, and Opera. As soon as put in, a brand new icon that includes a small browser emblem within the backside proper nook is added to the smartphone’s residence display screen, mainly serving as an internet site hyperlink. An instance is proven in Determine 2, the place we examine the icon of a PWA on the left aspect with an icon of a typical app on the correct aspect.

PWAs are basically a sort of app, however in contrast to conventional apps which might be downloaded and put in from an app retailer, PWAs are accessed and used immediately inside an internet browser. They’re constructed utilizing frequent internet programming languages akin to HTML (for construction), CSS (for design), and JavaScript (for interactivity), that are the identical applied sciences used to create web sites. PWAs are recognized for his or her compatibility and suppleness, as they’re designed to work on any machine that has a standards-compliant internet browser. Which means that a consumer, whether or not on a desktop pc, laptop computer, pill, or smartphone, can entry the identical PWA while not having to obtain a separate app for every machine.
If a PWA is put in from a phishing web site, its icon is prone to mimic that of a reputable banking utility, with the slight addition of a small browser icon. Upon launching this malicious PWA, a full-screen phishing web site is displayed that requests the consumer’s banking credentials.
WebAPKs
Subsequently, the risk actor improved on this assault state of affairs, persevering with to focus on purchasers of the identical banks as earlier than however using a extra superior sort of PWA referred to as a WebAPK. WebAPKs are Android apps which might be routinely generated by the Chrome browser when customers add a PWA to their Android machine’s residence display screen. To differentiate between these two, PWAs are apps constructed utilizing internet applied sciences, whereas WebAPKs use a know-how to combine PWAs as native Android apps. What’s completely different about WebAPKs is that they seem extra like native Android apps than typical PWAs, as a result of their icons shouldn’t have the small browser emblem that PWA icons have. This absence of a browser emblem can lead a consumer to mistakenly consider {that a} malicious WebAPK is a reputable app, as illustrated in Determine 3.

The distribution scheme stayed the identical – customers have been capable of obtain and set up a standalone app from phishing web sites, as an alternative of merely a PWA internet shortcut. The WebAPK requires guide set up; nevertheless, the consumer is just not requested to grant specific permission to put in apps from unknown sources or to permit the browser to put in unknown apps, as this isn’t an everyday app. Due to that, customers may not remember that they’re putting in an app from an untrusted supply. Determine 4 reveals an instance of what it seems like when customers go to a phishing web site that asks them to replace and set up a malicious WebAPK.
As soon as it’s put in and opened, the malicious app requests banking credentials. Extra particulars about phishing campaigns that use PWAs and WebAPKs have been mentioned in our earlier blogpost.
NGate malware
On March sixth, 2024 we found that NGate Android malware turned obtainable on the identical distribution domains that have been beforehand used to facilitate phishing campaigns delivering malicious PWAs and WebAPKs.
After being put in and opened, NGate shows a faux web site that asks for the consumer’s banking data, which is then despatched to the attacker’s server. Along with its phishing capabilities, NGate malware additionally comes with a instrument referred to as NFCGate, which is misused to relay NFC information between two units – the machine of a sufferer and the machine of a perpetrator. The NFCGate instrument was developed by college students from the Safe Cellular Networking Lab on the Technical College of Darmstadt in Germany and is offered on GitHub. NFCGate’s important operate is to transmit an NFC sign from one Android machine by way of a server to a different Android machine that may mimic or emulate it, as depicted in Determine 5.
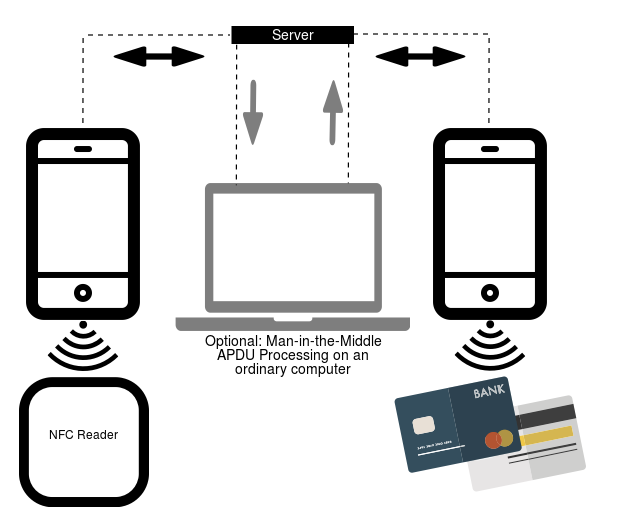
NFCGate is a instrument that may work together with NFC visitors on a tool. On the machine the place NFCGate is put in, it will probably:
1. Seize NFC visitors from apps that use NFC.
2. Move alongside or relay this NFC information from one machine to a different.
3. Mimic or replay information it has beforehand intercepted, on the opposite machine.
A few of these options work solely on rooted units; nevertheless, relaying NFC visitors is feasible from non-rooted units as properly. The NGate malware misuses solely considered one of NFCGate’s options. It doesn’t intervene with different information that’s obtainable on the compromised machine, and doesn’t attempt to mimic it. It abuses NFCGate solely to go alongside NFC information from one machine to a different.
Nonetheless, NGate additionally prompts its victims to enter delicate data like their banking shopper ID, date of start, and the PIN code for his or her banking card. It additionally asks them to activate the NFC function on their smartphone. Then, victims are instructed to position their fee card in the back of their smartphone till the malicious app acknowledges the cardboard.
What’s occurring behind the scenes is that the NFC information from the sufferer’s financial institution card is being despatched by way of a server to the attacker’s Android machine. Basically, this enables the attacker to imitate the sufferer’s financial institution card on their very own machine. This implies the attacker can now use this copied card information on their Android machine to make funds and withdraw cash from an ATMs that use NFC.
Full assault state of affairs with a backup answer
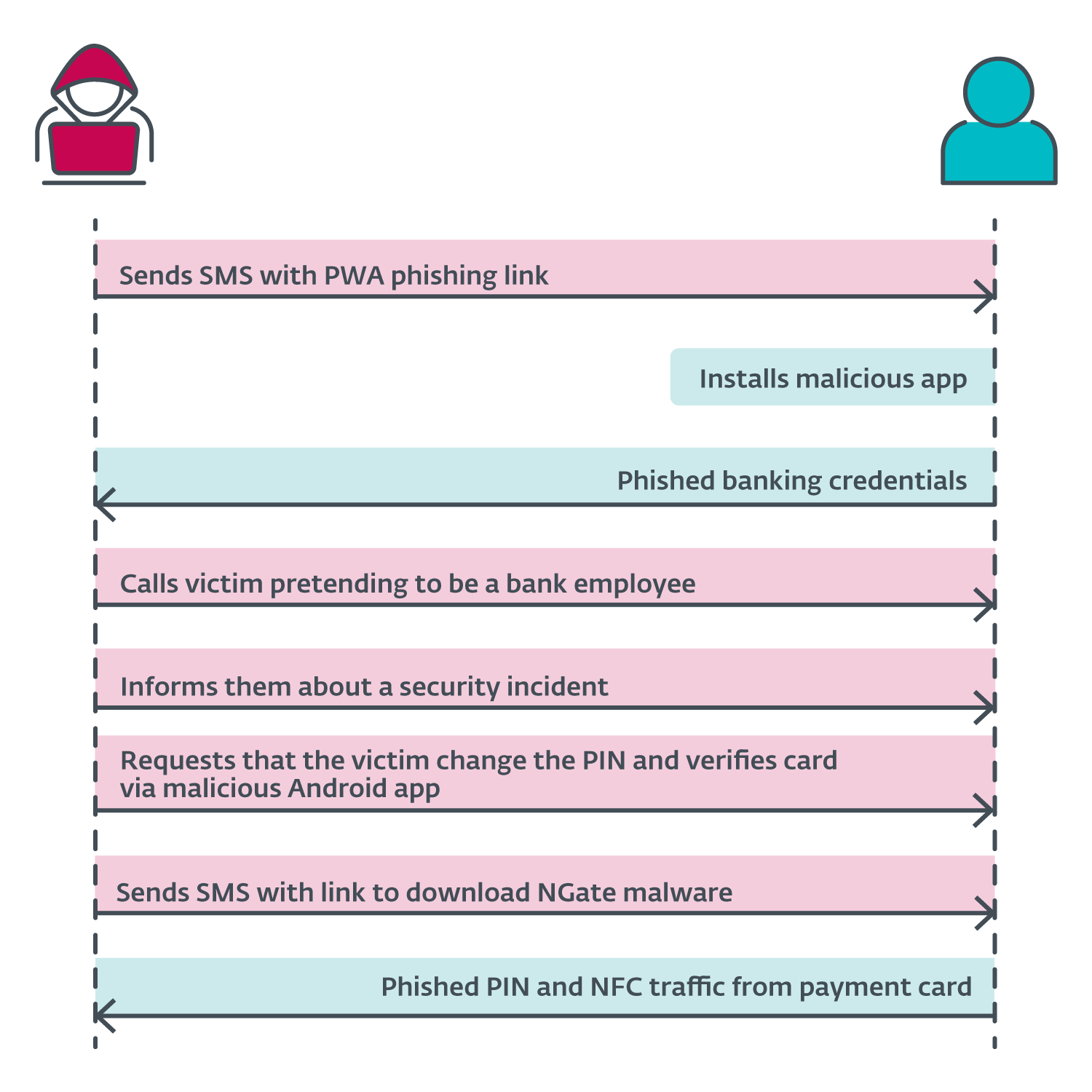
The announcement by the Czech police revealed the assault state of affairs began with the attackers sending SMS messages to potential victims a couple of tax return, together with a hyperlink to a phishing web site impersonating banks. These hyperlinks almost certainly led to malicious PWAs. As soon as the sufferer put in the app and inserted their credentials, the attacker gained entry to the sufferer’s account. Then the attacker referred to as the sufferer, pretending to be a financial institution worker. The sufferer was knowledgeable that their account had been compromised, seemingly as a result of earlier textual content message. The attacker was truly telling the reality – the sufferer’s account was compromised, however this reality then led to a different lie.
To “defend” their funds, the sufferer was requested to vary their PIN and confirm their banking card utilizing a cell app – NGate malware. A hyperlink to obtain NGate was despatched through SMS. We suspect that inside the NGate app, the victims would enter their previous PIN to create a brand new one and place their card in the back of their smartphone to confirm or apply the change.
Because the attacker already had entry to the compromised account, they may change the withdrawal limits. If the NFC relay technique didn’t work, they may merely switch the funds to a different account. Nonetheless, utilizing NGate makes it simpler for the attacker to entry the sufferer’s funds with out leaving traces again to the attacker’s personal checking account. A diagram of the assault sequence is proven in Determine 6.
Different attainable assault situations
The utilization of NGate malware or a custom-made model of NFCGate opens up the chance for extra assault situations, significantly in conditions the place the risk actor has bodily entry and will doubtlessly clone NFC tags or fee playing cards. To carry out and emulate the next attainable assaults, the attacker requires a rooted and customised Android machine.
Gaining entry through NFC tags
An NFC tag or token is a compact, contactless machine that has the flexibility to retailer and switch information. These tags can serve a wide range of functions, together with identification and information switch. NFC tags can be utilized as playing cards for public transportation, worker ID playing cards for entry management in buildings, wearable well being/affected person monitoring units, and so forth.
Each NFC tag has a singular ID (UID) and a knowledge part the place keys are saved. When these tags are positioned close to a card reader, a handshake happens, verifying that the tag has the proper keys for authorization. Nonetheless, some readers solely confirm the UID of the token for authorization, bypassing the necessity for the keys. The UID is usually 4 bytes lengthy.
Any non-rooted Android machine can learn NFC tags that adjust to ISO/IEC 14443. Nonetheless, solely sure rooted Androids can emulate the UID of an NFC tag. Due to this fact, if a reader verifies solely the token UID, it’s attainable to make use of NFCGate to relay and emulate the tag. If a reader requires additionally the keys (saved within the information part) for authentication, NFCGate is unable to repeat them, making it not possible to clone an NFC tag in such a case.
Which means that an attacker, both with bodily entry to a supported NFC tag or by tricking a consumer to place the tag in the back of the smartphone the place this malicious app is put in, can duplicate the UID of the NFC entry token. This could then be used to emulate the UID and achieve entry to restricted areas, buildings, workplaces, and comparable areas.
Throughout our testing, we efficiently relayed the UID from a MIFARE Basic 1K tag, which is usually used for public transport tickets, ID badges, membership or pupil playing cards, and comparable use circumstances. Utilizing NFCGate, it’s attainable to carry out an NFC relay assault to learn an NFC token in a single location and, in actual time, entry premises in a distinct location by emulating its UID, as proven in Determine 7.
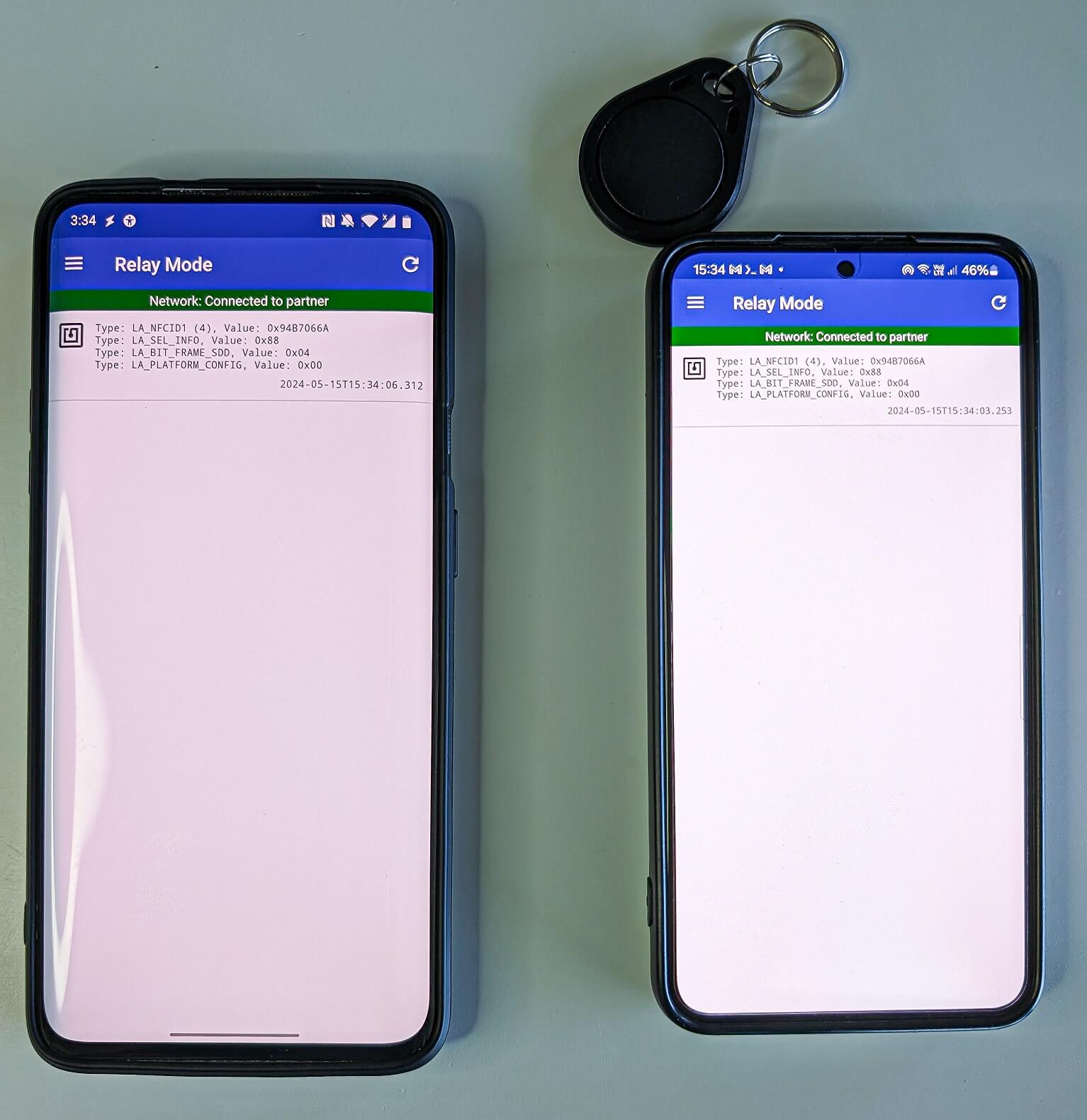
Nonetheless, after we tried to emulate the UID, NFCGate despatched completely different UIDs to the reader as an alternative of the relayed UID. We found that our testing machine (OnePlus 7 Professional) is on the listing of units that don’t help UID cloning. In consequence, we used the NFC Card Emulator Professional (Root) app and manually entered the UID to efficiently clone it.
This assault state of affairs is extremely focused, that means that the attacker must already know the place the token can be utilized.
Small contactless funds through fee playing cards
Along with the method utilized by the NGate malware, an attacker with bodily entry to fee playing cards can doubtlessly copy and emulate them. This method could possibly be employed by an attacker trying to learn playing cards by way of unattended purses, wallets, backpacks, or smartphone circumstances that maintain playing cards, significantly in public and crowded locations.
This state of affairs, nevertheless, is usually restricted to creating small contactless funds at terminal factors, relying on the restrict set by the financial institution that issued the cardboard, not for ATM withdrawals, because the latter would require the attacker to have the cardboard’s PIN.
One other theoretical state of affairs entails cloning a fee card saved in smartphone pockets apps. It’s attainable to relay the NFC sign from Android smartphones geared up with pockets apps, akin to Google Pockets. Nonetheless, as of April 2024, Google requires customers to offer verification for each NFC fee. Due to this fact, even with an unlocked machine, a consumer would nonetheless want to offer verification within the Google Pockets app earlier than making a fee. Equally, the Apple Pockets app additionally requests authorization earlier than processing a fee. These safety measures make it more difficult to relay and emulate fee playing cards from the Google and Apple pockets apps, utilizing the NFCGate instrument.
Technical evaluation of NGate malware
Preliminary entry
Preliminary entry to the machine is gained by deceiving the sufferer into putting in a malicious app, typically below the guise of a false assertion that there’s an overpayment of revenue tax that the sufferer can reclaim. This request is usually delivered through SMS and we consider these messages have been despatched to random telephone numbers. Sadly, we weren’t capable of purchase samples of those SMS messages, and no screenshots have been made publicly obtainable by the Czech authorities.
Ought to victims obtain the app and enter their credentials, the attacker then initiates a telephone name, posing as a financial institution worker. They inform the victims that their accounts have been compromised and advise them to vary their PINs and confirm their banking playing cards utilizing a distinct app. This new app, offered through one other SMS hyperlink, incorporates the NGate malware. Not one of the malicious apps we analyzed have been obtainable on Google Play.
We discovered two domains, mimicking the Czech Raiffeisenbank (as depicted in Determine 8) and the ČSOB financial institution, the place NGate was obtainable for obtain. On the time of writing, none of them have been lively:
- raiffeisen-cz[.]eu
- app.mobil-csob-cz[.]eu
![Figure 8. One of the distribution websites (raiffeisen-cz[.]eu) for NGate malware](https://web-assets.esetstatic.com/wls/2024/8-2024/ngate/figure8.png)
Toolset
The NGate malware shows uniform traits throughout all six samples we analyzed. Every pattern shares the identical bundle identify (rb.system.com) and makes use of the identical hardcoded phishing URL that’s distinctively recognized with a singular ID (present in the important thing question parameter) to show particular internet content material. All samples have been signed utilizing the identical developer certificates (SHA-1 fingerprint: 0C799950EC157BB775637FB3A033A502F211E62E). This constant sample throughout all six samples signifies a uniformity of their improvement and deployment.
The entire samples function the identical hardcoded phishing URL (https://shopper.nfcpay.employees[.]dev/?key=8e9a1c7b0d4e8f2c5d3f6b2); nevertheless, every app has a definite key related to it. This distinctive key corresponds to a particular banking phishing web site that’s exhibited to the potential sufferer. The given hyperlink serves solely as a redirection to the meant phishing web site. From the samples analyzed, we have been capable of establish 5 distinct phishing web sites, particularly:
- rb.2f1c0b7d.tbc-app[.]life
- geo-4bfa49b2.tbc-app[.]life
- rb-62d3a.tbc-app[.]life
- csob-93ef49e7a.tbc-app[.]life
- george.tbc-app[.]life
The icon and identify of every pattern has been designed to imitate particular focused banking apps, additional enhancing their misleading look.
Upon initiation, the NGate malware presents the sufferer with a phishing web site inside a WebView. A WebView is basically a window or mini browser inside the utility itself. It’s used to show internet content material or internet pages with out having to depart the appliance or open a separate internet browser. On this case, the web site requests the consumer’s private data, akin to shopper ID and date of start, as depicted in Determine 9.
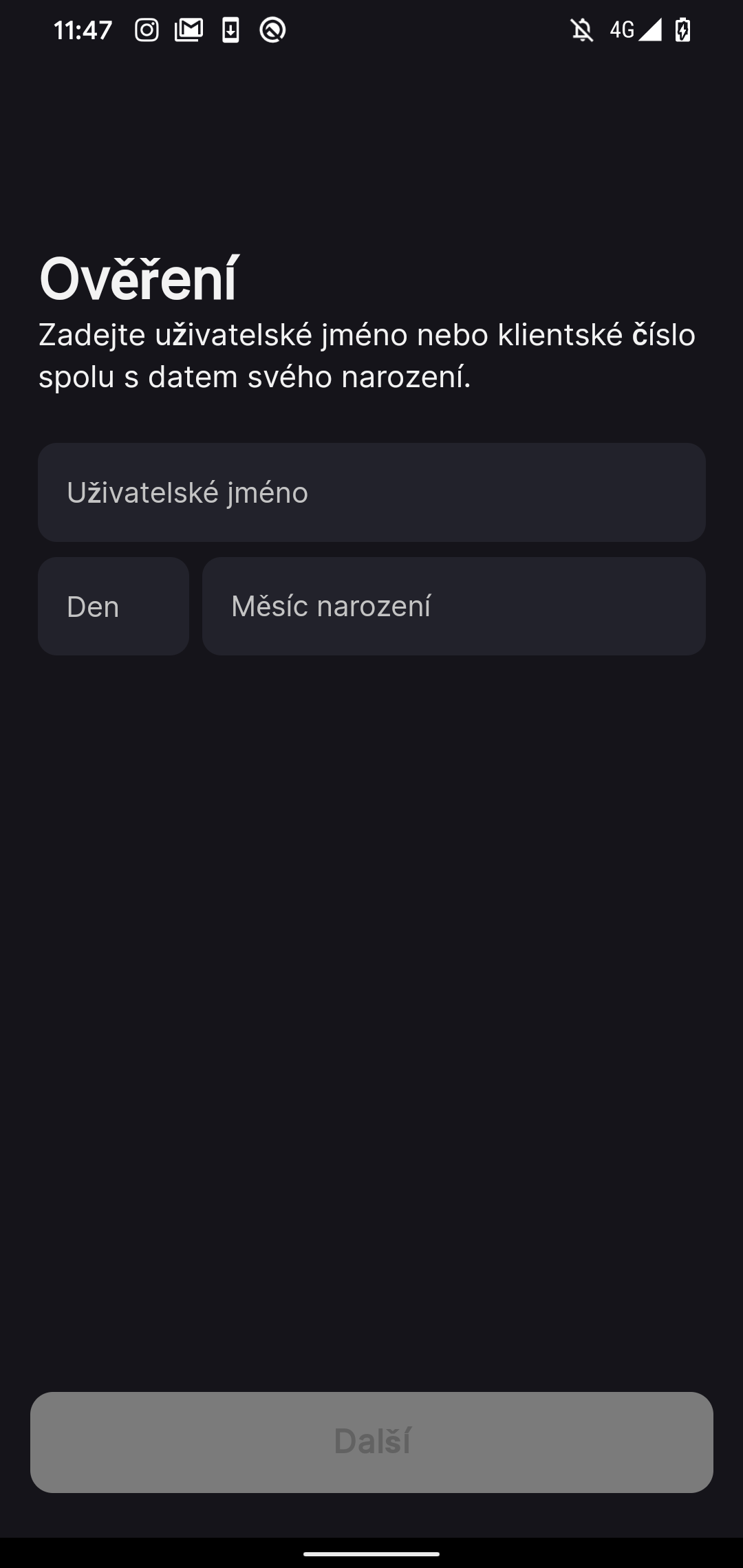
The misleading phishing web site guides the sufferer to not solely enter the PIN code for his or her banking card, but additionally to allow the NFC function on their machine. The sufferer is then instructed to place their card on the bottom of their smartphone, setting the stage for an NFC relay assault.
In contrast to typical malware, NGate doesn’t obtain particular directions from a Command and Management (C&C) server. As an alternative, the compromised machine is managed through the phishing web site. That is achieved by way of the usage of a JavaScript interface that triggers sure Android capabilities. These capabilities embrace retrieving details about the machine such because the mannequin and the NFC standing, establishing a server to which the NFC visitors will likely be redirected, and initiating the NFC relay assault.
Determine 10 illustrates a code snippet of a operate that’s tasked with establishing an NFC relay server and enabling the machine to learn after which ahead NFC visitors.
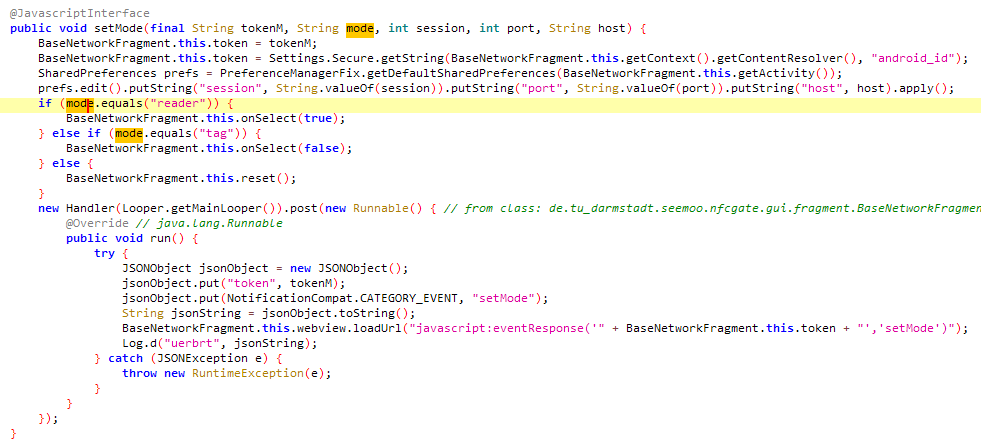
NGate makes use of two distinct servers to facilitate its operations. The primary is a phishing web site designed to lure victims into offering delicate data and able to initiating an NFC relay assault. The second is an NFCGate relay server tasked with redirecting NFC visitors from the sufferer’s machine to the attacker’s. In our preliminary evaluation of the NGate samples, we discovered that the NFC server could possibly be set primarily based on the response from the phishing web site. Nonetheless, in subsequent samples, these servers gave the impression to be hardcoded into the NGate malware.
If the sufferer follows all of the directions issued by NGate, it ends in the attacker being able to relay the NFC visitors from the sufferer’s fee card. This permits the attacker to make use of the sufferer’s monetary data to withdraw funds or make funds at contactless terminals.
Prevention
Making certain security from such advanced assaults requires the usage of sure protecting steps towards techniques like phishing, social engineering, and Android malware. These steps embrace:
- Checking the web site’s authenticity. This may be performed by wanting on the URL to ensure the web site isn’t a faux model of a real one.
- Solely downloading apps from official sources, such because the Google Play retailer. This precaution considerably reduces the danger of unknowingly putting in dangerous software program.
- Preserving fee card PIN codes secret. This necessary data needs to be stored protected always.
- Utilizing safety apps on cell units that may cease doubtlessly undesirable software program and malware, like NGate, from being downloaded and put in. These safety apps add an additional layer of protection by constantly scanning and monitoring for threats.
- Turning off the NFC operate on units when it’s not wanted. This step helps to stop any unauthorized entry or information switch through NFC.
- Utilizing protecting circumstances or protectors for radio frequency identification (RFID) playing cards. By making a barrier that blocks undesirable RFID scans, these can cease anybody from stealing NFC information from the cardboard.
- Utilizing digital variations of bodily playing cards on smartphones. These digital playing cards are saved securely on the machine and might be protected by further safety measures, akin to biometric authentication, making them a safer and extra handy different to conventional plastic playing cards.
Conclusion
ESET researchers have investigated a novel and distinctive assault state of affairs that mixes well-known strategies, akin to phishing, with a brand new malware strategy of relaying NFC visitors from victims’ bodily fee playing cards to the attackers’ Android cell machine. Earlier than transitioning to the brand new malware, which we named NGate, to relay NFC visitors, the attackers previously used PWA, then WebAPKs, to steal the banking credentials of their victims. This evolution showcases the attackers’ willpower and elevated effort in executing their fraudulent operations.
Whereas we’ve got recognized and completely examined one particular assault state of affairs, it’s essential to notice that theoretically there could possibly be further misuse circumstances. These might contain the cloning of bodily playing cards or accessing NFC tokens, which might doubtlessly amplify the risk and its impacts.
This crimeware marketing campaign was targeted on Czechia and is at present on maintain, seemingly as a result of arrest of a suspected perpetrator. Nonetheless, the potential for its enlargement into different areas or international locations can’t be dominated out. Moreover, the arrest of 1 participant with substantial money available offers tangible proof of the real-world penalties of those “digital” crimes. Due to this fact, it’s important to stay conscious of social engineering techniques, keep cautious on-line, and use strong cell safety apps.
For any inquiries about our analysis revealed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis provides non-public APT intelligence studies and information feeds. For any inquiries about this service, go to the ESET Risk Intelligence web page.
IoCs
A complete listing of Indicators of Compromise (IoCs) and samples might be present in our GitHub repository.
Recordsdata
|
SHA-1 |
Filename |
Detection |
Description |
|
7225ED2CBA9CB6C038D8 |
csob_smart_klic.apk |
Android/Spy.NGate.B |
NGate Android malware. |
|
66DE1E0A2E9A421DD16B |
csob_smart_klic.apk |
Android/Spy.NGate.C |
NGate Android malware. |
|
DA84BC78FF2117DDBFDC |
george_klic.apk |
Android/Spy.NGate.C |
NGate Android malware. |
|
E7AE59CD44204461EDBD |
george_klic-0304.apk |
Android/Spy.NGate.C |
NGate Android malware. |
|
103D78A180EB973B9FFC |
rb_klic.apk |
Android/Spy.NGate.A |
NGate Android malware. |
|
11BE9715BE9B41B1C852 |
rb_klic.apk |
Android/Spy.NGate.C |
NGate Android malware. |
Community
|
IP |
Area |
Internet hosting supplier |
First seen |
Particulars |
|
91.222.136[.]153 |
raiffeisen-cz[.]eu |
Internet hosting Ukraine LTD |
2024‑03‑05 |
NGate distribution web site. |
|
104.21.7[.]213 |
shopper.nfcpay.employees[.]dev |
Cloudflare, Inc. |
2024‑03‑03 |
Phishing web site. |
|
172.187.98[.]211 |
N/A |
Divya Quamara |
2024‑04‑07 |
NGate C&C server. |
|
185.104.45[.]51 |
app.mobil-csob-cz[.]eu |
Internet hosting Ukraine LTD |
2024‑03‑12 |
NGate distribution web site. |
|
185.181.165[.]124 |
nfc.cryptomaker[.]information |
Serverius |
2024‑02‑21 |
NGate C&C server. |
MITRE ATT&CK methods
This desk was constructed utilizing model 15 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Identify |
Description |
|
Preliminary Entry |
Phishing |
NGate has been distributed utilizing devoted web sites impersonating reputable companies. |
|
|
Credential Entry |
Enter Seize: GUI Enter Seize |
NGate tries to acquire victims’ delicate data through a phishing WebView pretending to be a banking service. |
|
|
Discovery |
System Info Discovery |
NGate can extract details about the machine together with machine mannequin, Android model, and details about NFC. |
|
|
Command and Management |
Utility Layer Protocol: Internet Protocols |
NGate makes use of a JavaScript interface to ship and execute instructions to compromised units. |
|
|
Non-Normal Port |
NGate makes use of port 5566 to speak with its server to exfiltrate NFC visitors. |
||
|
Out of Band Information |
NGate can exfiltrate NFC visitors. |



