
South Korea’s Nationwide Cyber Safety Middle (NCSC) warns that state-backed DPRK hackers hijacked flaws in a VPN’s software program replace to deploy malware and breach networks.
The advisory connects this exercise with a nationwide industrial factories modernization venture Kim Jong-un, the North Korean president, introduced in January 2023, believing the hackers need to steal commerce secrets and techniques from South Korea.
The 2 menace teams implicated on this exercise are Kimsuky (APT43) and Andariel (APT45), state-sponsored actors beforehand linked to the infamous Lazarus Group.
“The Info Neighborhood attributes these hacking actions to the Kimsuky and Andariel hacking organizations below the North Korean Reconnaissance Common Bureau, noting the unprecedented nature of each organizations focusing on the identical sector concurrently for particular coverage aims,” warns the NCSC.
Trojanized updates and installers
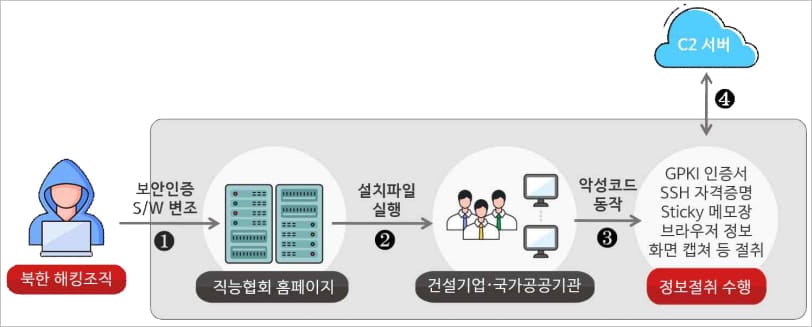
Within the first case highlighted within the advisory, dated January 2024, Kimsuky compromised the web site of a South Korean building commerce group to disseminate malware to guests.
In keeping with a February report by ASEC, when staff tried to log into the group’s web site, they had been prompted to put in required safety software program referred to as “NX_PRNMAN” or “TrustPKI.”
These trojanized installers had been digitally signed with a sound certificates from Korean protection firm “D2Innovation,” successfully bypassing antivirus checks.
When the trojanized software program was put in, the malware was additionally deployed to seize screenshots, steal knowledge saved in browsers (credentials, cookies, bookmarks, historical past), and steal GPKI certificates, SSH keys, Sticky Notes, and FileZilla knowledge.
This marketing campaign contaminated the methods of South Korean building firms, public establishments, and native governments.
Supply: NCSC
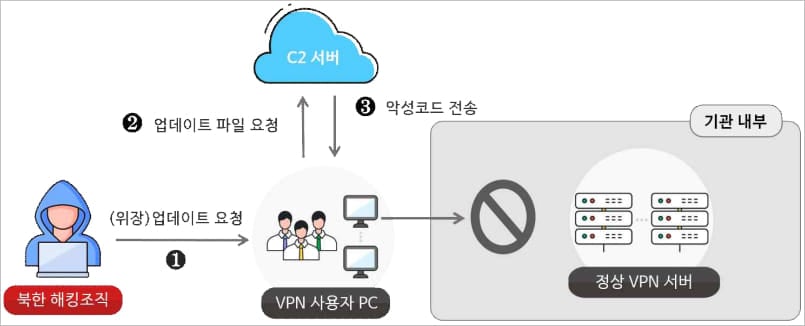
The second case occurred in April 2024, when the NCSC says the Andariel menace actors exploited a vulnerability in a home VPN software program’s communication protocol to push out faux software program updates that set up the DoraRAT malware.
“In April 2024, the Andariel hacking group exploited vulnerabilities in home safety software program (VPN and server safety) to switch replace information with malware, distributing distant management malware named “DoraRAT” to building and equipment firms,” explains a machine-translated model of the NCSC advisory.
The NCSC says the vulnerability allowed the menace actors to spoof packets to customers’ PCs, which misidentified them as reputable server updates, permitting the malicious variations to be put in.
DoraRAT is a light-weight distant entry trojan (RAT) with minimal performance that enables it to function extra stealthily.
The variant noticed within the specific assault was configured for stealing giant information, resembling equipment and tools design paperwork, and exfiltrating them to the attacker’s command and management server.
Supply: NCSC
The NCSC says operators of internet sites vulnerable to being focused by state-sponsored hackers ought to request safety inspections from Korea’s Web & Safety Company (KISA).
Moreover, it is strongly recommended that strict software program distribution approval insurance policies be carried out and administrator authentication be required for the ultimate distribution stage.
Different generic recommendation contains well timed software program and OS updates, ongoing worker safety coaching, and monitoring authorities cybersecurity advisories to determine and cease rising threats rapidly.

