The Chinese language firm accountable for handing out domains ending in “.high” has been given till mid-August 2024 to point out that it has put in place methods for managing phishing experiences and suspending abusive domains, or else forfeit its license to promote domains. The warning comes amid the discharge of latest findings that .high was the commonest suffix in phishing web sites over the previous yr, second solely to domains ending in “.com.”

Picture: Shutterstock.
On July 16, the Web Company for Assigned Names and Numbers (ICANN) despatched a letter to the homeowners of the .high area registry. ICANN has filed a whole lot of enforcement actions in opposition to area registrars over time, however on this case ICANN singled out a site registry answerable for sustaining a complete top-level area (TLD).
Amongst different causes, the missive chided the registry for failing to answer experiences about phishing assaults involving .high domains.
“Based mostly on the data and data gathered via a number of weeks, it was decided that .TOP Registry doesn’t have a course of in place to promptly, comprehensively, and fairly examine and act on experiences of DNS Abuse,” the ICANN letter reads (PDF).
ICANN’s warning redacted the title of the recipient, however data present the .high registry is operated by a Chinese language entity referred to as Jiangsu Bangning Science & Expertise Co. Ltd. Representatives for the corporate haven’t responded to requests for remark.
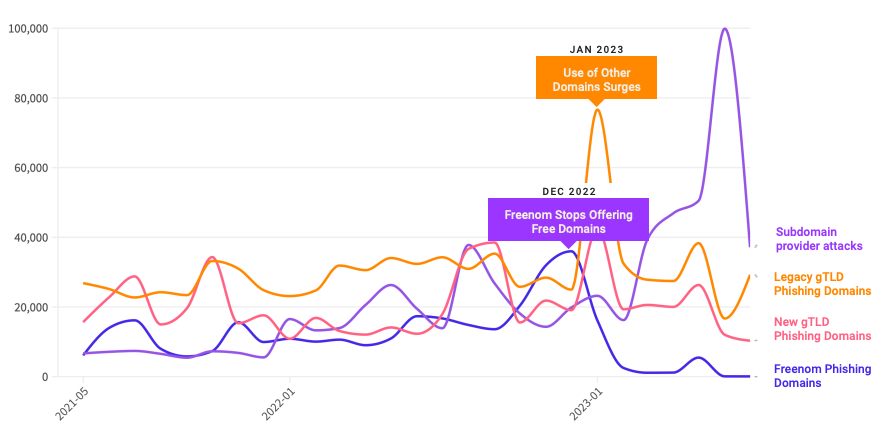
Domains ending in .high have been represented prominently in a brand new phishing report launched right this moment by the Interisle Consulting Group, which sources phishing knowledge from a number of locations, together with the Anti-Phishing Working Group (APWG), OpenPhish, PhishTank, and Spamhaus.
Interisle’s latest research examined practically two million phishing assaults within the final yr, and located that phishing websites accounted for greater than 4 p.c of all new .high domains between Might 2023 and April 2024. Interisle mentioned .high has roughly 2.76 million domains in its steady, and that greater than 117,000 of these have been phishing websites previously yr.
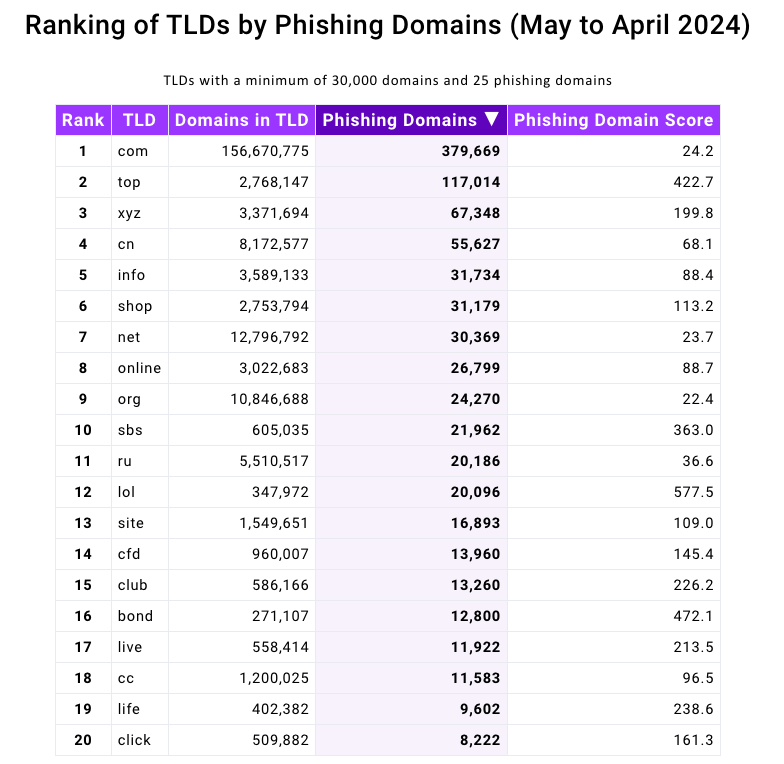
Supply: Interisle Consulting Group.
ICANN mentioned its evaluation was primarily based on data collected and studied about .high domains over the previous few weeks. However the truth that excessive volumes of phishing websites are being registered via Jiangsu Bangning Science & Expertise Co Ltd. is hardly a brand new development.
For instance, greater than 10 years in the past the identical Chinese language registrar was the fourth commonest supply of phishing web sites, as tracked by the APWG. Keep in mind that the APWG report excerpted beneath was printed greater than a yr earlier than Jiangsu Bangning acquired ICANN approval to introduce and administer the brand new .high registry.
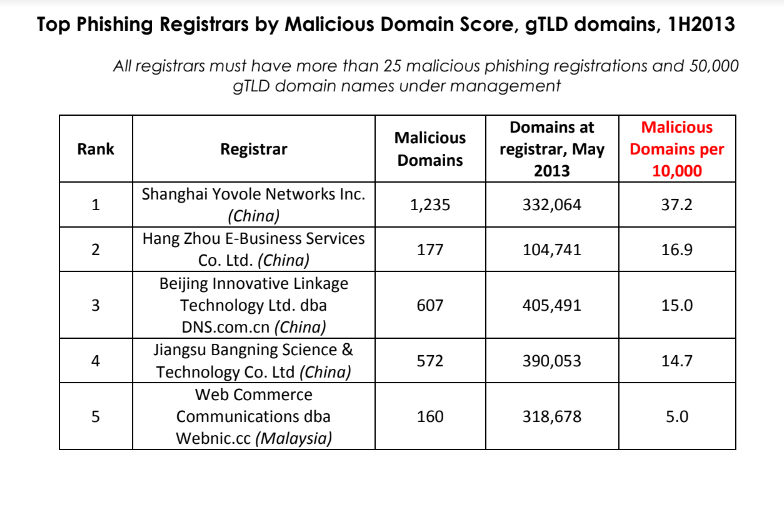
Supply: APWG phishing report from 2013, two years earlier than .high got here into being.
A captivating new wrinkle within the phishing panorama is the expansion in rip-off pages hosted by way of the InterPlanetary File System (IPFS), a decentralized knowledge storage and supply community that’s primarily based on peer-to-peer networking. In response to Interisle, using IPFS to host and launch phishing assaults — which might make phishing websites tougher to take down — elevated a staggering 1,300 p.c, to roughly 19,000 phishing websites reported within the final yr.
Final yr’s report from Interisle discovered that domains ending in “.us” — the top-level area for america — have been among the many most prevalent in phishing scams. Whereas .us domains are usually not even on the High 20 record of this yr’s research, “.com” maintained its perennial #1 spot as the most important supply of phishing domains total.
A yr in the past, the phishiest area registrar by far was Freenom, a now-defunct registrar that handed out free domains in a number of country-code TLDs, together with .tk, .ml, .ga and .cf. Freenom went out of enterprise after being sued by Meta, which alleged Freenom ignored abuse complaints whereas monetizing visitors to abusive domains.
Following Freenom’s demise, phishers rapidly migrated to different new low-cost TLDs and to companies that enable nameless, free area registrations — notably subdomain companies. For instance, Interisle discovered phishing assaults involving web sites created on Google’s blogspot.com skyrocketed final yr greater than 230 p.c. Different subdomain companies that noticed a considerable development in domains registered by phishers embrace weebly.com, github.io, wix.com, and ChangeIP, the report notes.
Interisle Consulting companion Dave Piscitello mentioned ICANN may simply ship comparable warning letters to a minimum of a half-dozen different top-level area registries, noting that spammers and phishers are likely to cycle via the identical TLDs periodically — together with .xyz, .information, .help and .lol, all of which noticed significantly extra enterprise from phishers after Freenom’s implosion.
Piscitello mentioned area registrars and registries may considerably cut back the variety of phishing websites registered via their companies simply by flagging prospects who attempt to register big volumes of domains directly. Their research discovered that a minimum of 27% of the domains used for phishing have been registered in bulk — i.e. the identical registrant paid for a whole lot or 1000’s of domains in fast succession.
The report features a case research wherein a phisher this yr registered 17,562 domains over the course of an eight-hour interval — roughly 38 domains per minute — utilizing .lol domains that have been all composed of random letters.
ICANN tries to resolve contract disputes privately with the registry and registrar group, and specialists say the nonprofit group often solely publishes enforcement letters when the recipient is ignoring its personal notices. Certainly, ICANN’s letter notes Jiangsu Bangning didn’t even open its emailed notifications. It additionally cited the registry for falling behind in its ICANN membership charges.
With that in thoughts, a evaluation of ICANN’s public enforcement exercise suggests two traits: One is that there have been far fewer public compliance and enforcement actions in recent times — even because the variety of new TLDs has expanded dramatically.
The second is that in a majority of circumstances, the failure of a registry or registrar to pay its annual ICANN membership charges was cited as a motive for a warning letter. A evaluation of practically two dozen enforcement letters ICANN has despatched to area registrars since 2022 reveals that failure to pay dues was cited as a motive (or the motive) for the violation a minimum of 75 p.c of the time.
Piscitello, a former vice chairman of safety at ICANN, mentioned practically all breach notices despatched out whereas he was at ICANN have been as a result of the registrar owed cash.
“I feel the remainder is simply lipstick to recommend that ICANN’s on high of DNS Abuse,” Piscitello mentioned.
KrebsOnSecurity has sought remark from ICANN and can replace this story in the event that they reply.
ICANN mentioned most of its investigations are resolved and closed via the preliminary casual decision stage, and that a whole lot of enforcement circumstances are initiated throughout this stage with the contracted events who’re required to reveal compliance, turn out to be compliant, and/or current and implement remediation plans to stop the recurrence of these enforcement points.
“You will need to take note of that, previous to issuing any discover of breach to a registrar or registry operator, ICANN Compliance conducts an total contractual compliance ‘well being verify’ of the related contracted social gathering,” ICANN mentioned in a written response to questions. “Throughout this verify, ICANN Compliance proactively critiques the contracted social gathering’s compliance with obligations throughout the agreements and insurance policies. Any extra contractual violation discovered throughout these checks is added to the Discover of Breach. It isn’t unusual for events who did not adjust to contractual obligations (whether or not they’re associated to DNS Abuse, RDDS, or others) to even be in arrears with ICANN charges.”
Replace, 11:49 p.m. ET: Added assertion from ICANN. Clarified Piscitello’s former position at ICANN.