A distributed denial-of-service (DDoS) assault focusing on a monetary establishment within the United Arab Emirates set information all through the cyberattack and the sustained quantity of requests.
The assault — attributed to pro-Palestinian hacktivist group BlackMeta, also called DarkMeta — lasted six days and included a number of waves of Internet requests lasting anyplace from 4 to twenty hours, focusing on the monetary establishment’s web site. Total, it lasted greater than 100 hours in whole, averaging 4.5 million requests per second, cybersecurity agency Radware acknowledged in an advisory revealed this week.
The DDoS assault represents a big departure from the usual hacktivist denial-of-service assaults, says Pascal Geenens, director of risk intelligence for Radware.
“These assaults had been lasting between 60 seconds and 5 minutes — they got here, they hit onerous, and so they go away after one to 5 minutes,” he says. “Now, within the case of this assault, the marketing campaign in whole lasted six days, and in these six days, 70% of the time, that buyer was being focused by a median of 4.5 million requests.”
BlackMeta, also called SN_BlackMeta, appeared in November 2023 and has a historical past of claiming duty for assaults towards organizations in Israel, the United Arab Emirates, and the USA. In Could, the group claimed duty for a multiday denial-of-service assault on the San Francisco-based Web Archive. In April, the group claimed to have attacked the Israel-based infrastructure of the Orange Group, a French supplier of telecommunication companies in Europe, the Center East, and Africa. The group additionally focused organizations in Saudi Arabia, Canada, and the United Arab Emirates.
DDoS Assaults for $500 a Month
The BlackMeta group introduced its intent to assault the monetary establishment on Telegram within the days main as much as the operation. The cyberattack inundated the monetary agency’s web site with requests, inflicting the share of official requests to plummet to as little as 0.002%, with a median of 0.12%. The assaults continued for 70% of the time through the six-day interval.
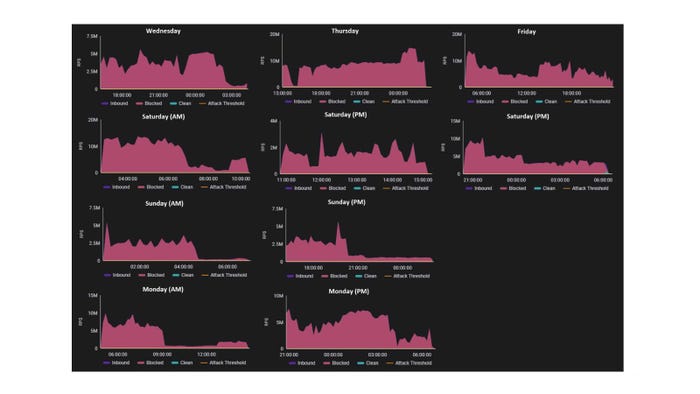
Bandwidth captures displaying the assault over six days. Supply: Radware
The attackers used a cybercrime service generally known as InfraShutdown, which permits attackers to focus on websites for $500 to $625 every week, in keeping with Radware’s advisory.
BlackMeta is primarily motivated by a pro-Palestinian ideology, however just like Nameless Sudan, has an anti-Western stance, and seems to have hyperlinks with Russia, and makes use of Arabic, English, and Russian in its posts, Radware acknowledged.
“The group positions its assaults as retribution for perceived injustices towards Palestinians and Muslims,” the corporate acknowledged. “Their targets usually embody crucial infrastructure corresponding to banking techniques, telecommunication companies, authorities web sites and main tech corporations, all reflecting a method to disrupt entities considered as complicit in or supportive of their adversaries.”
Benefiting from DDoS Service?
BlackMeta is probably going a rebrand of Nameless Sudan, a bunch that made a reputation for itself final 12 months attacking targets together with the loose-knit pro-Russian Killnet group, in keeping with the researchers. Nameless Sudan focused Israeli organizations and the encrypted messaging service Telegram in 2023. Evaluating the variety of claimed assaults by month over the previous 12 months and a half exhibits Nameless Sudan’s exercise dwindling on the similar time that BlackMeta’s was ramping up.
Nameless Sudan marketed its InfraShutdown DDoS assault service throughout earlier assaults, urging different would-be attackers to enroll, which suggests the group is probably going financially benefiting from its “hacktivism.”
“If the actors behind [BlackMeta] are in any manner associated to or help Nameless Sudan, the premium InfraShutdown service is very prone to be the origin of the 14.7 million [requests-per-second], 100-hour assault marketing campaign,” Radware acknowledged in its advisory
Price-limiting the bandwidth throughout such assaults isn’t an answer to sustained application-layer assaults, as a result of an organization would have to have the ability to differentiate between the 1.5 billion official requests reaching the web site over a six-day interval, and the 1.25 trillion malicious requests focusing on the positioning, Geenens says.
“With the assaults going to Layer 7 — the appliance layer — the issue has shifted,” he says. “Earlier than we had been on the community stage, you possibly can use a firewall, however that’s an excessive amount of processing energy, so we moved to community safety. However while you transfer one layer up [to Layer 7], they will goal particular pages and randomize the queries that they put in, so that they make it seem like official posts.”


